How Risk Management and Compliance Are Connected

When running a business of any size, risk management and compliance are of the utmost … How Risk Management and Compliance Are Connected

When running a business of any size, risk management and compliance are of the utmost … How Risk Management and Compliance Are Connected

Data breaches are among modern companies’ worst nightmares. They can spell disaster for businesses and … What to Expect From a PCI Compliance Risk Assessment
Power outages, data loss, pandemics, or natural disasters can strike at any time and seriously … Defining Business Continuity vs. Disaster Recovery

At the heart of every successful enterprise is a great staff. To grow and become … Your Guide to Risk Management During the Employee Lifecycle

Every company strives to prepare for worst-case scenarios, but some disasters aren’t the result of … 6 Vital Business Continuity Best Practices

Compliance vs. Risk Management: Analyzing Their Comparative Roles in Your Organization Running a business comes … Compliance vs. Risk Management

7 Strategies To Increase Risk Awareness In 2012, the Harvard Business Review wrote that incorrect … How To Increase Risk Awareness

Unlocking the Benefits of Systematic Vendor Management: Why It Matters for Your Business Success Vendor … 5 Key Reasons Why a Systematic Approach to Vendor Management is Critical for Your Business Success

The Importance of User Access Management: Best Practices To Consider It’s always a good feeling … Understanding User Access Management
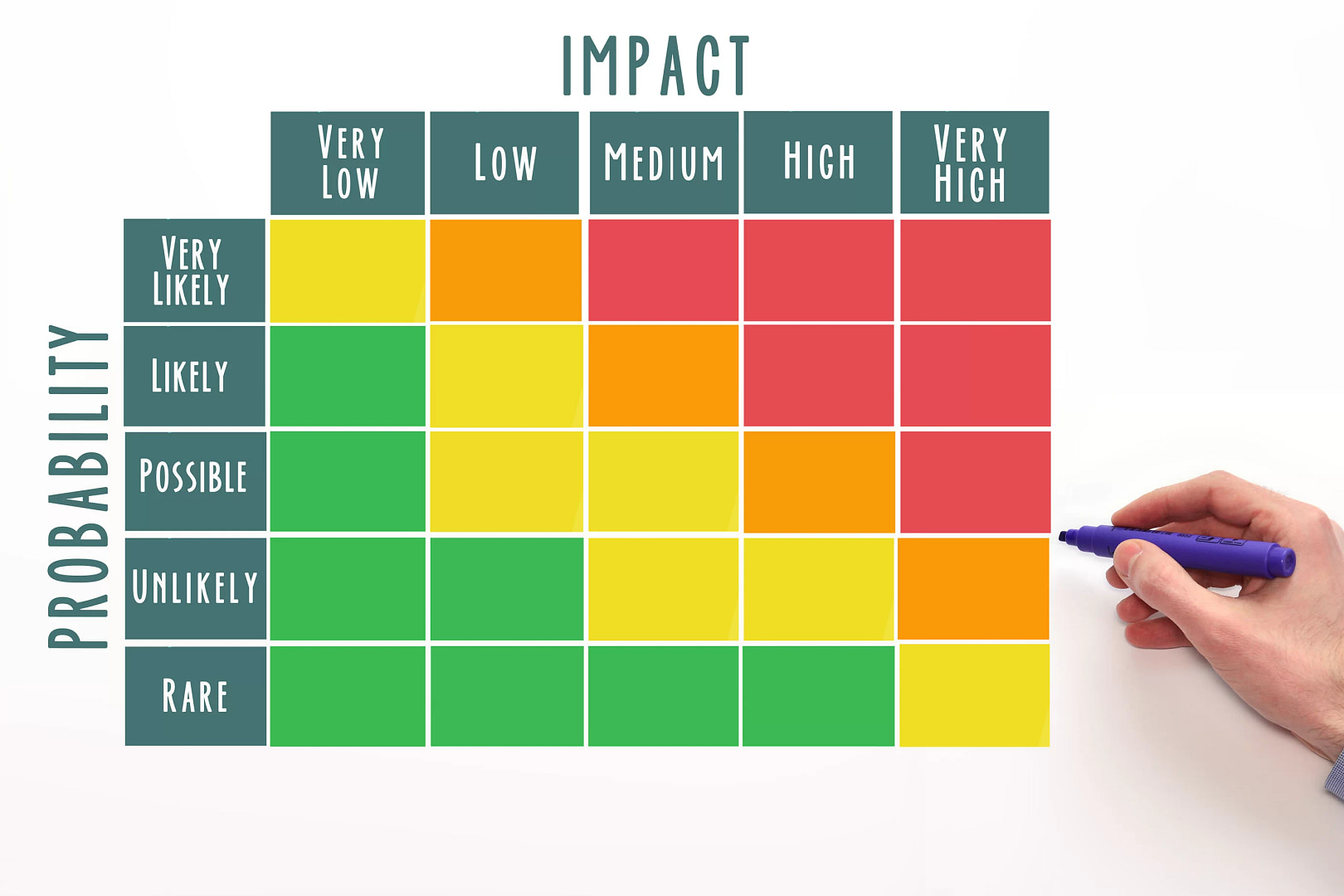
What Should Be Included in a Risk Assessment Report? Risk assessment should be an integral … What To Include in a Risk Assessment Report