Compyl Secures Series A Funding – Learn More About Our Next Chapter!
This is not a “checkbox” SOC 2 exercise. Compyl empowers organizations to maintain SOC 2 compliance at all times.
For any business that must protect stakeholder data, security is a make-or-break mission. Over the past decade, a SOC 2 certification has become an industry-wide standard of excellence for data security. Achieving and maintaining SOC 2 status is a formidable challenge. Helping your business surmount that test is Compyl’s mission.
What is SOC 2 certification? In 2010, the Association of International Certified Professional Accountants released a standard outlining three categories of Service Organization Controls:
With its focus on data security, the SOC 2 standard empowered IT service providers to build confidence among customers and stand out from competitors. The stamp of approval from a respected accounting firm spurred many IT CEOs to learn how to get SOC 2 certification.

Compyl works with the tech your organization uses today. From AWS to Workday, and nearly every platform in between, this service seamlessly integrates from day one. Unlike cookie-cutter approaches, Compyl extracts critical data and transposes the information wherever and whenever your organization needs it.
Compyl’s unique query language cross-references data from multiple sources to uncover granular details otherwise missed. Powerful and user-friendly, these checks can be set to run as frequently as your business model requires.
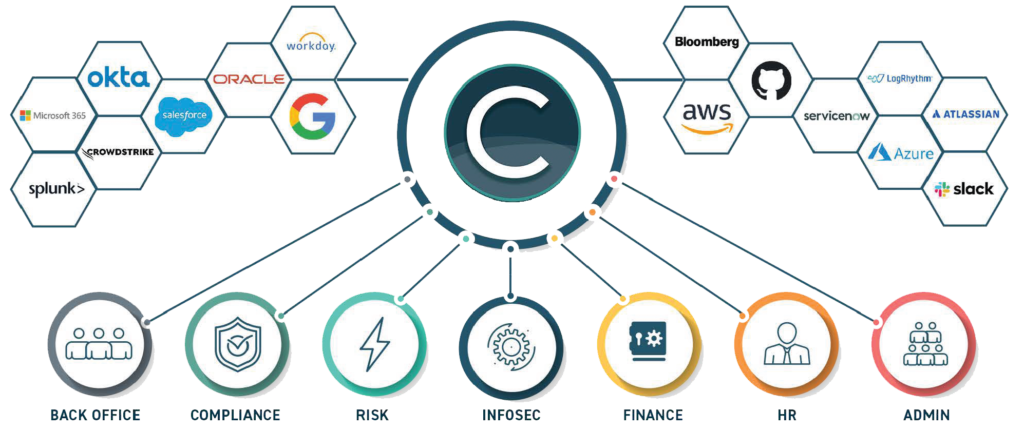
As organizations grow, they encounter new challenges. Ad-hoc course corrections are a prescription for failure. Compyl’s comprehensive data-gathering capability powers the security processes that win and retain customers.
The Compyl team understands every nuance of the SOC 2 audit process. We know that every business is unique and requires custom-tailored control processes. With Compyl as your partner, your business will gain security practices and mitigation policies for the long haul.
SOC 2 compliance has become one of the most sought-after security milestones for growing SaaS organizations. See how Compyl puts SOC 2 status within reach.
Say goodbye to patchwork solutions and manage your organization’s compliance and security programs with a single platform.
Compyl assigns ownership and tracks the progress of each control. Your business gains visibility during the SOC 2 journey and accountability for every team member.
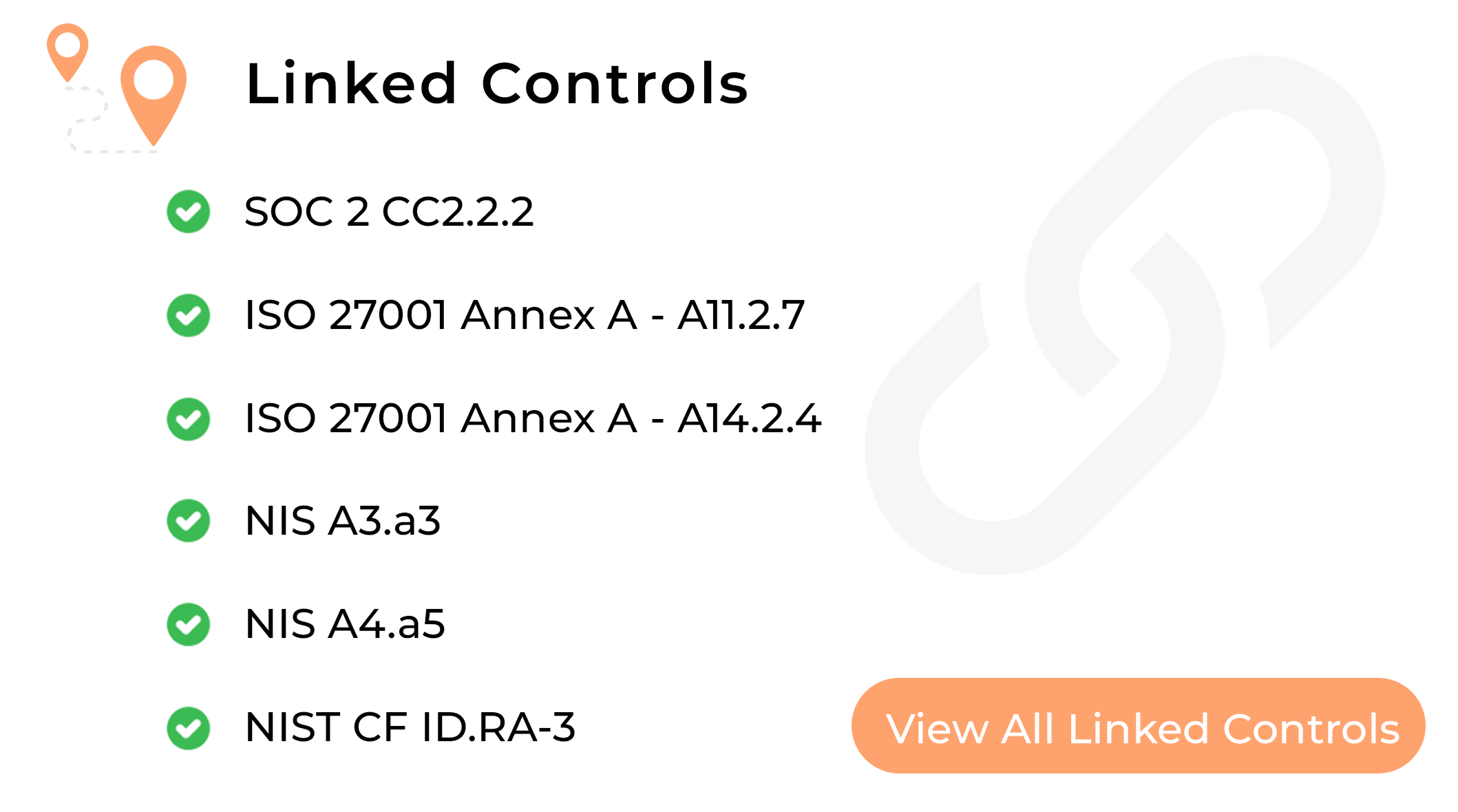
Frameworks evolve constantly. Compyl ensures your business will keep stride by mapping your proven controls with new frameworks.
Evidence is the cornerstone of a successful audit. Compyl flags redundancies, eliminates error-prone manual tasks and streamlines evidence gathering with automation.
Security gaps may cause catastrophic damage to your business. The Compyl team can build a scalable security program for businesses in any growth stage.
Compyl's timely alerts will keep your enterprise in step with industry regulations.
To gain a SOC 2 certification, a business prepares a comprehensive report on its data security processes and then submits the document to an audit by an AICPA member firm. Inside the SOC 2 category, the AICPA outlines two types of reports:
Type I reports provide a snapshot of a business’s control processes for a single moment.
Type II reports cover the effectiveness of control efforts for a period ranging from one to 12 months. The AICPA recommends a monitoring period of at least six months, but many enterprises now monitor year-round.
Every business must include the Security criterion in their SOC 2 report and may include any of the other four categories depending on their service model. Only a few elite and deep-pocketed enterprises undergo an audit for all five criteria.
SOC 2 audits last for weeks and involve hundreds of evidence requests. If the audit produces a clean bill of health, known in the accounting industry as an unqualified opinion, a business may market itself as a SOC 2 Type II vender.
For an IT vendor or software-as-a-service provider, a one-time successful SOC 2 audit will not suffice in today’s competitive environment. Annual SOC 2 audits have become routine.
SOC 2 status means more than a report and a badge for your website. Savvy customers have learned to spot any effort to game audits, and you can expect that prospective clients will scrutinize your audited report before signing on. While SOC 2 status can aid marketing, a business must maintain a relentless focus on the processes that earn and maintain the standard.
Scaling hikes the difficulty level for each successive SOC 2 audit. Every growing IT business will add employees, gain new customers and confront evolving security threats. Without robust processes, each of these challenges creates opportunities for security gaps. These lapses in turn trigger reputation damage, lost customers and even lawsuits. Stakes this high require a one-of-a-kind solution: Compyl.

An all-in-one streamlined solution created by information security experts.











