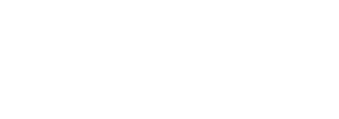Compyl 26.1 Is Live — See What’s New and How GRC Just Got Faster.
Your GRC should too.
Turn your data into deep GRC insights and AI-guided action with the flexibility you need to proactively manage risk, stay compliant and adapt to your needs—no heavy lift required.
Our latest release (26.1) delivers real-time visibility, intelligent automation, and AI-powered execution—built to move at the speed of your work.
Interactive dashboards, automated evidence, and connected controls deliver real-time insight - no screenshots, no manual chasing.
Get fast answers, surface vendor risks, and finalize drafted security questionnaires so you stay focused on priorities and impact.




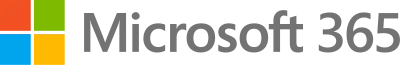




Avoid incidents and fines with real-time insights based on live, auditable evidence to catch issues that spreadsheets and other tools miss.
Save time by automating manual work while Compyl AI drafts risks, guides you to policy gaps and takes the first pass on questionnaires.
Leave rigid workflows, inflexible screens, and static reporting behind and adapt to your unique needs without coding or hassles.
Improve visibility and consistency across your business by centralizing your GRC program in a single, secure platform.
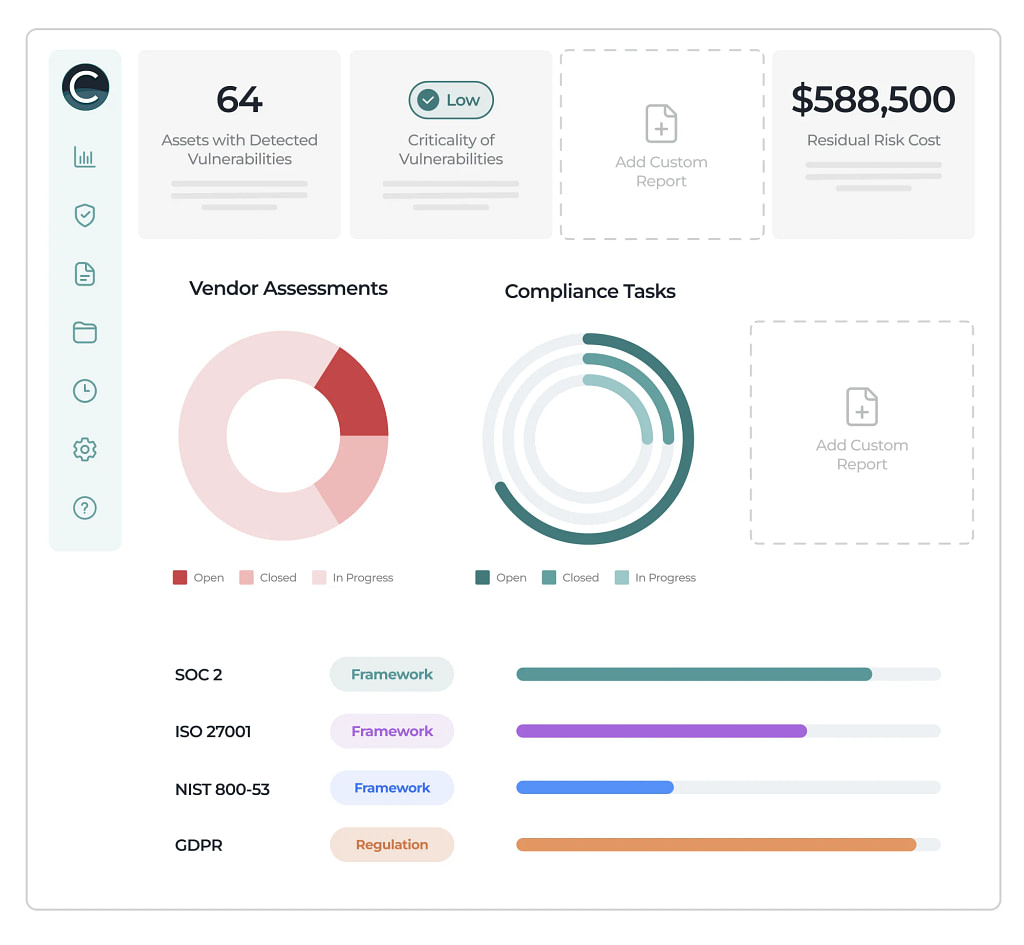
Get a real-time, complete view of GRC and be ready for every conversation with connected data and flexible reporting.
Capture data in the platform using 125+ integrations built in-house giving you
full access, without third-party risk.
See your real-time security posture based on live, auditable evidence to reduce risk and stay compliant.

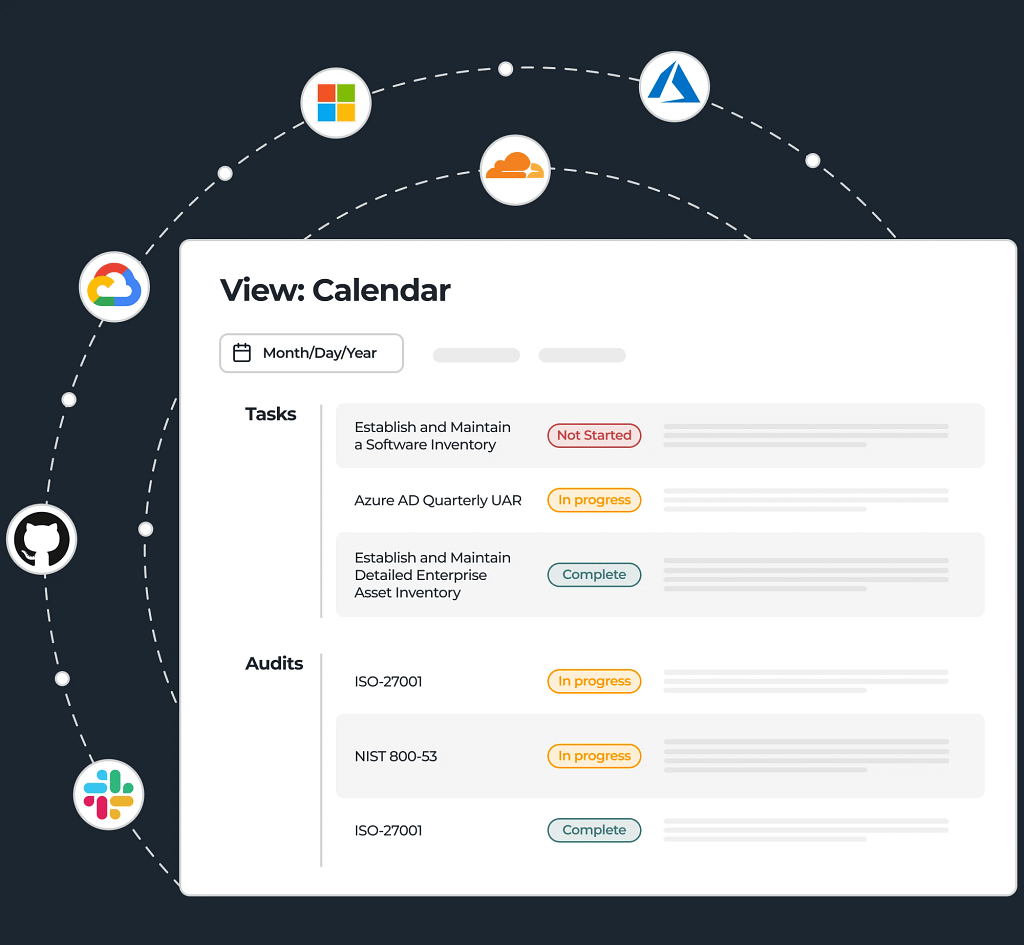
Ensure nothing slips through the cracks and monitor how work is progressing with task auto-creation and centralized task management.
Stop shuffling spreadsheets and free up time by integrating with existing systems to automate evidence collection, manual tasks and workflows.
Uncover issues in user access and security reviews by automatically combining data, routing reports, and creating tasks to fix issues with a click.
Refine, finalize and move faster by using Compyl AI to find information fast, conduct third-party risk intelligence and take the first pass at questionnaires.
Leave rigid structures behind by adjusting workflows, customizing
naming, and tailoring on-screen fields to support your team's way of working.
Show the information that matters most to you, your team and your stakeholders using pre-built, configurable dashboards or create your own, no coding required.
Be prepared for discussions at every level with visual, interactive KPIs and status charts, and out-of-the-box, configurable reporting with no coding.
Start where you are, mature your program and evolve as your needs change, without the burden of dedicated or costly resources.

“It is a very responsive team with great support and incredible AI capabilities to assist with managing policies, compliance, and risk.”
Mike Hamrah
Chief Security Officer

Continuous monitoring of your environments ensures that you are secure and compliant across all assets










Turn your data into deep GRC insights and AI-guided action with the flexibility you need to proactively manage risk, stay compliant and adapt to your needs—no heavy lift required.