Compyl Secures Series A Funding – Learn More About Our Next Chapter!
SOC 2 isn’t a set of hard and fast rules. Rather, it is a framework that sends a strong signal that an organization prioritizes key attributes: security, availability, processing integrity, confidentiality, and privacy. Completing a SOC 2 certification on its own is generally not enough to prove that you are 100% secure as an organization, but it’s a very good start and will go a long way toward instilling trust in your customers.
Developed by the American Institute of CPAs (AICPA), SOC 2 defines criteria for managing customer data based on five “trust service principles”
The foundational security principle, common to all audits.
Protection from unauthorized disclosure of sensitive data.
Protection that systems or data will be available as agreed or required.
Protection that systems or data are not changed in an unauthorized manner.
The use, collection, retention, disclosure, and disposal of personal information is protected.
Unlike ISO-27001, which has very rigid requirements, SOC 2 reports are unique to each organization. In line with specific business practices, each designs its own controls to comply with one or more of the trust principles.
These internal reports provide you (along with regulators, business partners, suppliers, etc.) with important information about how your service provider manages data.
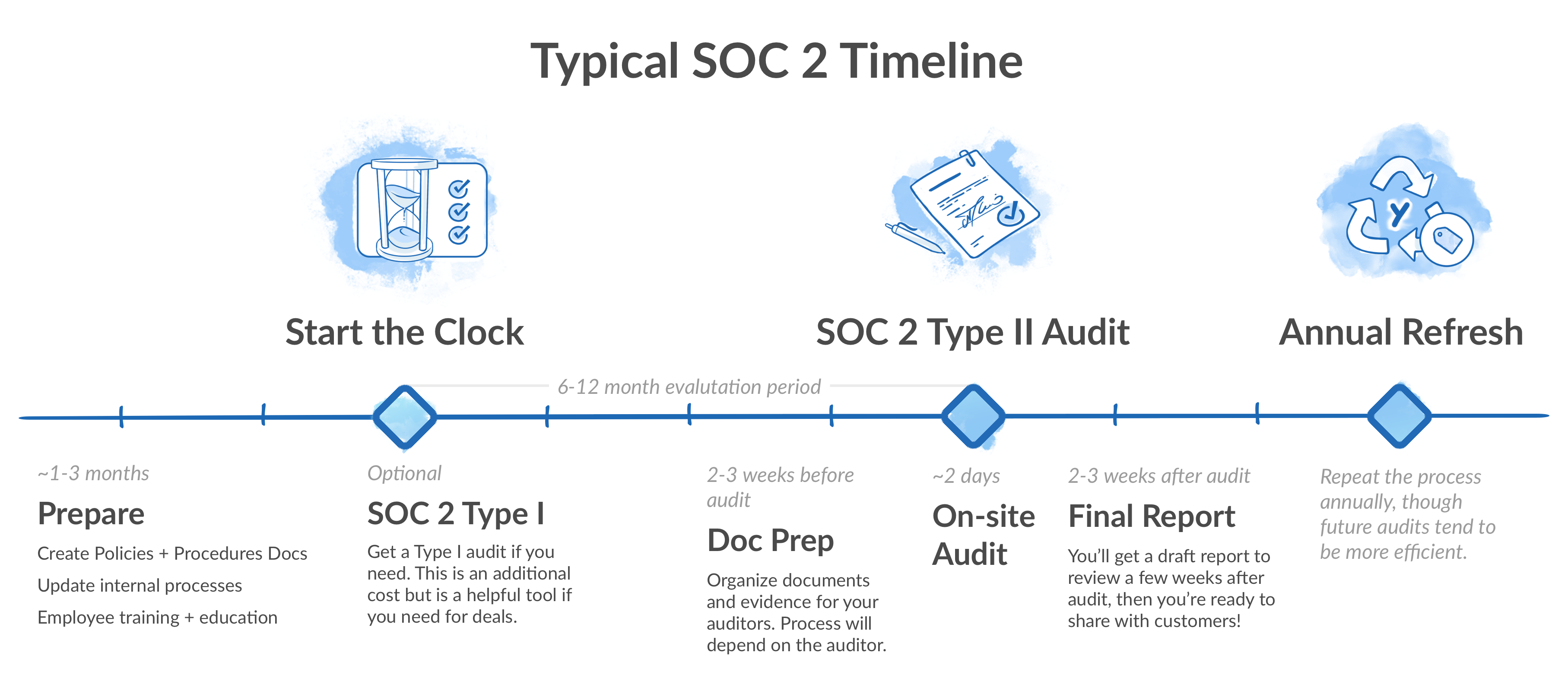
An audit conducted against the Trust Services Criteria standard at a single point in time. This audit answers: Are all the security controls that are in place today designed properly?
An audit conducted against the Trust Service Criteria standard over a period of time. This period typically covers six months the first time, and then a year thereafter. This means you’ll need a system of record. Type I reports are, as you might imagine, quicker to prepare for and conduct because you don’t have to wait for historical data over six months. However, while Type II reports take more time, they are also that much more valuable in the hands of customers, prospects, board members, partners, insurance companies, and so on. They report on what you’re actually doing, rather than what you aspire to do. Because of this added value, our recommendation is to get started early and work directly toward the Type II report. This approach emphasizes immediate action taken toward improving your security, and because Type II also covers Type I, there are financial savings in the long term if you start with Type II from day one.
The Common Criteria for Information Technology Security Evaluation, referred to as Common Criteria, is an internationally recognized standard for computer security certification. Common Criteria is a framework that assures that the process of specification, implementation, and evaluation of a computer security product has been rigorously tested in a repeatable manner. The goal of Common Criteria is for vendors to make claims about the security of their products and that independently run testing laboratories can determine if they meet those claims. Below are the nine Common Criteria that are typically associated with SOC 2 compliance for SaaS providers and vendors.
Framework: Management and Communications
Goal: Assure that management and the Board of Directors place a high value on integrity and security.
Details: Management is committed to the security of customer data and takes this into account when hiring personnel, evaluating processes and reporting compliance. The Board of Directors has independent oversight of the management team.
Activities and Deliverables: Ensure management understands SOC 2 and security and that they manage accordingly. CC1 is accomplished through onboarding procedures and ongoing training.
Additional Considerations: CC1.4 is to ensure your employees are competent and trained in security. This is accomplished through your onboarding plan and company workflows.
Software Recommended: HRIS such as BambooHR or Workday or HiBob


Framework: Management and Communications
Goal: Create quality policies and procedures to ensure customer data and operational security. Establish consistently reliable communications, both internally and externally.
Details: Your organization must generate and use quality information and documentation to ensure secure workflows and controls. It must also mandate proper communications across all departments and to external sources like vendors and customers.
Activities and Deliverables: Produce high-quality policies and procedures that are available through online documentation that is easily accessible to staff. Establish internal tools that will validate secure communication, both internally and externally.
Software Recommended: Notion, Google Docs, or other communication systems with audit functionality, but email also works.
Framework: Risk Assessment, Monitoring, and Control
Goal: Create clear objectives, analyze risks to achieve objectives, and monitoring how procedural changes impact risk.
Details: Specify organizational objectives enough so that personnel and management assess current and potential risks, including fraud. Develop procedures to update risk assessment when fundamental changes to internal systems take place.
Activities and Deliverables: Risk assessment processes that have corresponding documentation that is readily available to stake-holders. This includes regular updates and audits to both the risk assessment and the outcome of the evaluation.
Key Documents: Risk Assessment Tracking
Software Recommended: Notion, Google Docs, or Office


Framework: Risk assessment, monitoring, and control
Goal: Continually monitor, evaluate, and communicate the effectiveness of internal controls to accomplish the overall mission of securing data.
Details: Creating ongoing evaluations of controls that communicate deficiencies, both internally and externally, when appropriate. Activities and Deliverables: Evidence that shows risk control activities and defined risk management procedures.
Policies and Procedures: Notion, Google Docs, or other.
Software Recommended: Company workflows (usually department-specific) to easily export evidence (e.g., JIRA or Clubhouse for engineering, Github for infrastructure, AWS, etc.)
Framework: Risk assessment, monitoring, and control
Goal: Develop precise process controls and using technology to achieve company objectives while mitigating risk.
Details: The company develops controls for both workflow processes and technology tools to mitigate risk while still achieving pre-defined objectives. Also, defining transparent policies to establish expectations and procedures to ensure compliance.
Activities and Deliverables: Provide documentation showing risk control activities and proving risk management procedures were followed.
Key Documents: Risk Management Procedures Software Recommended: Technology Management that includes vendor management and related workflows to track employee activity, e.g. plus HRIS/Employee Tracking such as BambooHR, Workday to maintain physical access records.


Framework: The security of the physical premises where the organization houses data is the most important and in-depth.
Goal: Ensure only the right people have access to critical data, secure and encrypt data at all times, and physically protect servers storing data.
Activities and Deliverables: Providing sound security practices for physical servers, workstations, and employees, and evidence that these practices are working.
Software Recommended: Employee Access Control and On/Off-boarding procedures Compyl + Okta + HR Department
Framework: Robust Servers and Infrastructure
Goal: Ensure compliance systems are working; includes ongoing monitoring, incident response and evaluation, and disaster recovery.
Activities and Deliverables: Evidence showing Business Continuity and Disaster Recovery plans, and documentation showing that they work.
Key Documents: Business Continuity and Disaster Recovery Plan and Incident Reporting.
Software Recommended: Infrastructure systems such as AWS, Google Cloud, or Microsoft Azure


Framework: Infrastructure Change Management
Goal: Changes to technical infrastructure are well tested and approved before going live.
Details: The entity authorizes, designs, develops or acquires, configures, documents, tests, approves, and implements changes to any infrastructure, data, software, and procedures to meet its objectives.
Activities and Deliverables: Clear controls for how technical infrastructure (The System) changes, and evidence the changes were tested before going into production.
Software Recommended: Github for pull requests and a task manager such as ServiceNow or JIRA for engineering workflows.
Framework: Risk Mitigation and Vendor Management
Goal: Mitigate risk through defined business processes and vendor management.
Activities and Deliverables: Business Continuity, business insurance, vendor management, including vendor due diligence and management, especially for cloud-hosted vendors.
Key Documents: Vendor processes, assessments, and approval from key management personnel.
Recommended Software: SaaS Management Software such as Compyl can help mitigate risk across the organization.
SOC 2 certification is issued by outside auditors. They assess the extent to which a vendor complies with one or more of the five trust principles based on the systems and processes in place.
Trust principles are broken down as follows:
SOC 2 CC1: Control Environment Workflows are at the heart of every organization. As an organization grows from two people to five to ten, and so on, these workflows can introduce security loopholes.
SOC 2 CC1 addresses your control environment, of which workflows are a component. Most workflow suites includes predetermined workflows for the most common business tasks, including employee onboarding, offboarding, vendor requests, approvals, renewals, and terminations. It also includes the ability to build, save, and repeat your own customized workflows to match your particular internal processes. When you use Compyl for SOC 2 compliance, all your workflows are documented as exportable logs.
When you decide to undertake a SOC 2 audit, you can easily pull these logs and present them as evidence to your auditors.
SOC 2 CC5: Control Activities As mentioned earlier, the average mid-sized company uses 120 SaaS tools.
That’s a lot of vendors. Lack of visibility into who all these vendors are and how they interact with your company can be grounds for SOC 2 noncompliance. Maintaining unwieldy spreadsheets, while a common standard, fails to capture crucial real-time data regarding your vendors.
SOC 2 CC6: Logical and Physical Access Controls While the broader CC6 framework considers both logical and physical access controls, Compyl helps you manage logical access controls. We do this by giving you enhanced visibility of all the third-party apps in use at your organization. App discovery and tracking give you a single source of truth as support for your SOC 2 compliance documentation. Moreover, security monitoring provides ongoing access control data collection crucial to your SaaS security audit compliance. If a new app is added to your organization or there’s a user state change, Compyl captures this data as exportable activity logs.
SOC 2 CC9: Risk Mitigation One of the challenges companies face when creating a risk mitigation plan is the lack of a system of record. A system of record is a single source of truth providing transparent, auditable data about a process within an organization. Organizations using different SaaS products without a point of convergence struggle to create a unified system of record. Compyl solves this by providing a converged system of record comprising an extensive SaaS codex with a robust system of record.
The privacy principle addresses the system’s collection, use, retention, disclosure and disposal of personal information in conformity with an organization’s privacy notice, as well as with criteria set forth in the AICPA’s generally accepted privacy principles (GAPP). Personal identifiable information (PII) refers to details that can distinguish an individual (e.g., name, address, Social Security number). Some personal data related to health, race, sexuality and religion is also considered sensitive and generally requires an extra level of protection. Controls must be put in place to protect all PII from unauthorized access.
Adapt quickly to new industry requirements, expansion, and other needs that affect the organization.
To be able to get all the evidence needed for any audit in a single click is very important and can be a huge time saving for any industry and vertical.
Through this data, you can demonstrate the measures you have taken to modulate logical access control across all your organization’s apps. Using Compyl for SOC 2 compliance gives you a centralized view of all third-party SaaS apps in use in your organization, and tools to help you manage how your personnel interacts with them.
While SOC 2 compliance isn’t a requirement for SaaS and cloud computing vendors, its role in securing your data cannot be overstated.
An all-in-one streamlined solution created by information security experts.










