Want to See the Future of GRC? Check Out Evidence Studio.
A required framework for U.S. federal government agencies and contractors.
Compyl allows an organization to grow confidently while adapting rapidly to industry requirements, expansion, and other needs. Hence, NIST SP800-53’s baseline approach perfectly aligns with Compyl’s capabilities to continuously grow and enhance your control environment.
All U.S. federal government agencies and contractors must comply with NIST SP 800-53. Because the federal government trusts it, it is widely accepted by organizations and agencies from other industries too.
Compyl works with the tech your organization uses today. From AWS to Workday, and nearly every platform in between, this service seamlessly integrates from day one. Unlike cookie-cutter approaches, Compyl extracts critical data and transposes the information wherever and whenever your organization needs it.
Compyl’s unique query language cross-references data from multiple sources to uncover granular details otherwise missed. Powerful and user-friendly, these checks can be set to run as frequently as your business model requires.
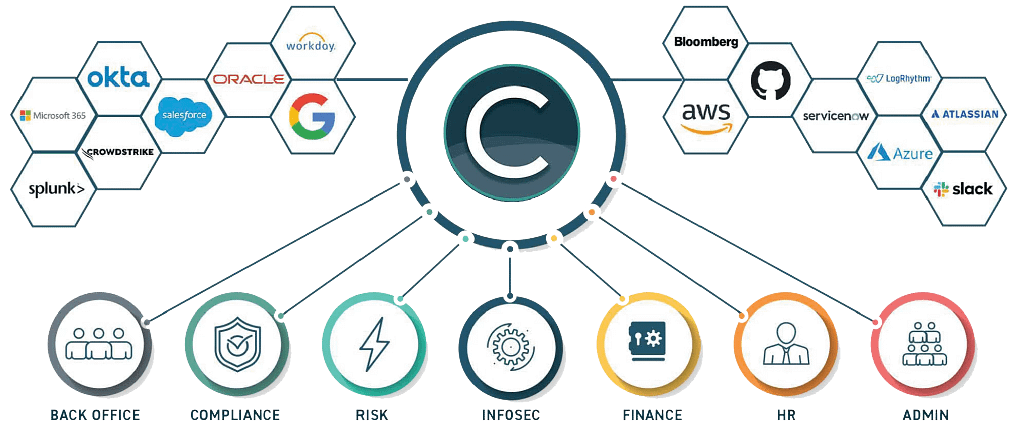
As organizations grow, they encounter new challenges. Compyl’s wide variety of functionality and flexibility allows our platform to be a true solution.
We have a team of experts that offer guidance along your security journey to ensure mitigation strategies are in place and best practices are always implemented.
The NIST SP 800-53 controls are classified into 18 control families and come with three security control baselines: low-impact, moderate-impact, and high-impact, as well as a privacy control baseline. This is a unique framework because it enables organizations to mature further as each control has its enhancements to meet the next baseline.
A single location to manage an organization's entire information security and compliance program.
Assign ownership and track the progress of each control. Maintain visibility during the entire NIST SP 800-53 journey.
A new level of efficiency. Quickly align with new frameworks or regulations by mapping similar controls to one another.
Reduce error-prone, redundant, manual tasks and streamline evidence gathering through Compyl's automation.
Compyl's platform puts a proper security program in place, and lets organizations focus on growing their business.
Adapt quickly to new industry requirements, expansion, and other needs that affect the organization.
An all-in-one streamlined solution created by information security experts.