Compyl Secures Series A Funding – Learn More About Our Next Chapter!
Experience unparalleled risk management, customization, scalability, and ease-of-use through our robust platform, surpassing the competition in every aspect.
Compyl stands out as the premier choice, offering unparalleled service and support for each of our valued customers. Discover why our track record of reliability and excellence makes us the preferred partner for organizations in need of security assurances.
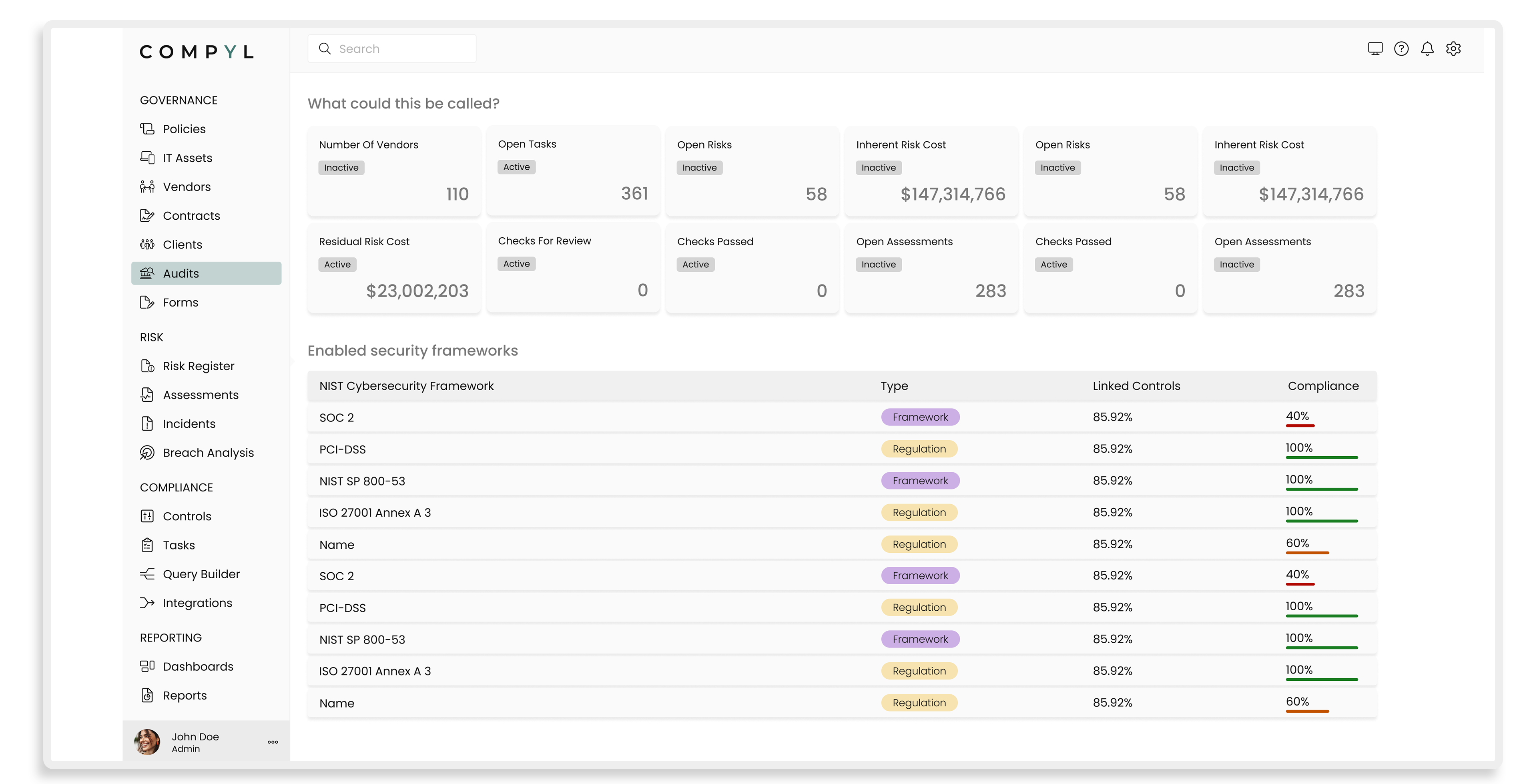

| Saas / Web | ||||||
| Mac | ||||||
| Windows | ||||||
| On-Premise |
| Agentless (no 3rd party software to install) |
| Dedicated Implementation Engineer | ||||||
| Dedicated Technical Information Security Officer | ||||||
| Dedicated Customer Success Agent |
| Live Chat |
| Offers API |
| One on One Training | ||||||
| Bi-Weekly Webinar | ||||||
| Documentation | ||||||
| Framework Agnostic |
| Alerts/Notifications | ||||||
| Auditor Portal | ||||||
| Audit Export w/ Evidence | ||||||
| Custom Dashboard Configuration | ||||||
| Custom Report Generation | ||||||
| Risk Assessment | ||||||
| Workflow Management | ||||||
| Archiving & Retention | ||||||
| Audit Management | ||||||
| Compliance Tracking | ||||||
| Control Testing | ||||||
| Auditing | ||||||
| Disaster Recovery | ||||||
| Vendor/Risk Management | ||||||
| Incident Management | ||||||
| Internal Controls Management | ||||||
| IT Risk Management | ||||||
| Operational Management | ||||||
| Policy Management | ||||||
Infosec and Compliance don’t have to be painful. See why our customers love the Compyl platform.
Move away from checklists and begin building a scalable security program.
Mature your security program with customization, automation, and support.
Centralize your security program with streamlined, automated efficiencies.
Scale your robust security environment with dedicated resources and guidance.