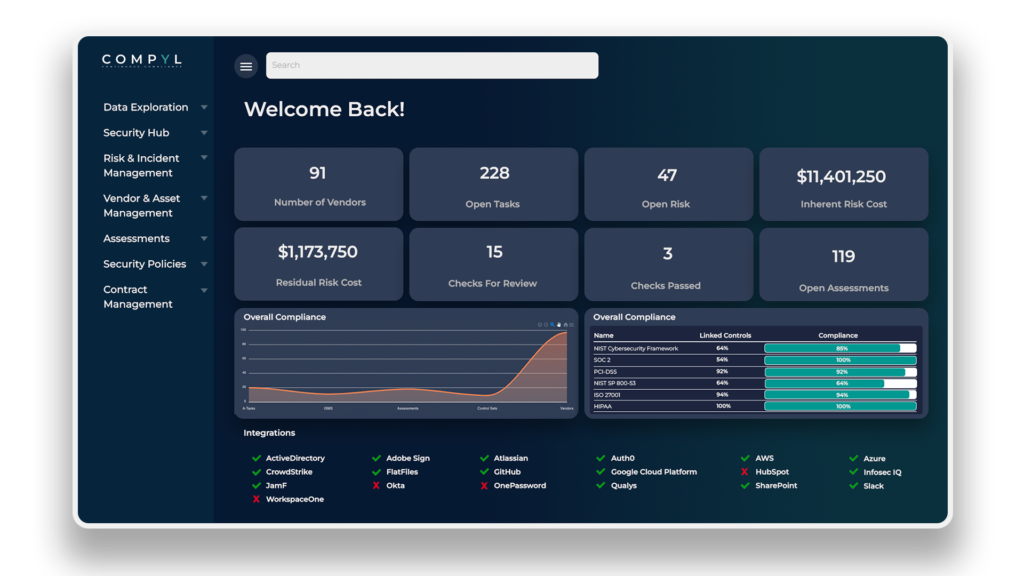
We are thrilled to unveil Compyl V5.0.0, a significant product update that is set to revolutionize the way you manage your security program. Today, we are excited to announce a host of new features that will elevate your experience with Compyl to unprecedented heights. Brace yourself for an upgraded look and feel, along with cutting-edge functionality driven by Artificial Intelligence (AI) technology. From AI-Powered Fields to Breach Analysis and enhanced contract management, this update introduces a wide range of capabilities designed to enhance your security program quickly and efficiently.
At Compyl, we are dedicated to empowering organizations to thrive in a secure and compliant environment. Our mission is to safeguard the integrity of valuable data assets while upholding trust with stakeholders. With V5.0.0, we take this commitment to a whole new level, delivering unparalleled solutions that redefine information security and compliance standards.
AI-Powered Fields
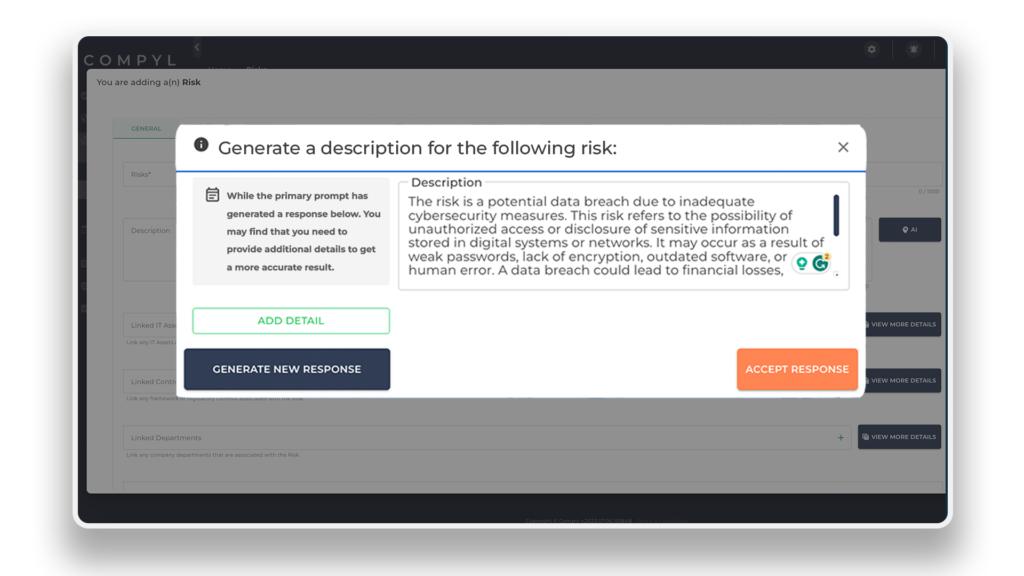
Compyl leverages the power of Artificial Intelligence (AI) to enhance its security processes. With AI integration, Compyl gains the ability to generate effective responses and detailed descriptions for essential security operations like risk mitigation plans and incident response plans. This integration enables companies to streamline security operations, improve decision-making, and enhance overall resilience against potential threats.
By utilizing AI throughout Compyl, users can automate and optimize the creation of risk mitigation plans. AI algorithms can analyze vast amounts of data, including historical security incidents, threat intelligence feeds, and regulatory compliance requirements. Based on this analysis, AI algorithms can generate comprehensive risk mitigation plans tailored to specific needs and industry standards. These plans outline proactive measures to identify, assess, and mitigate risks, ensuring that potential vulnerabilities are identified and addressed promptly.
Breach Analysis
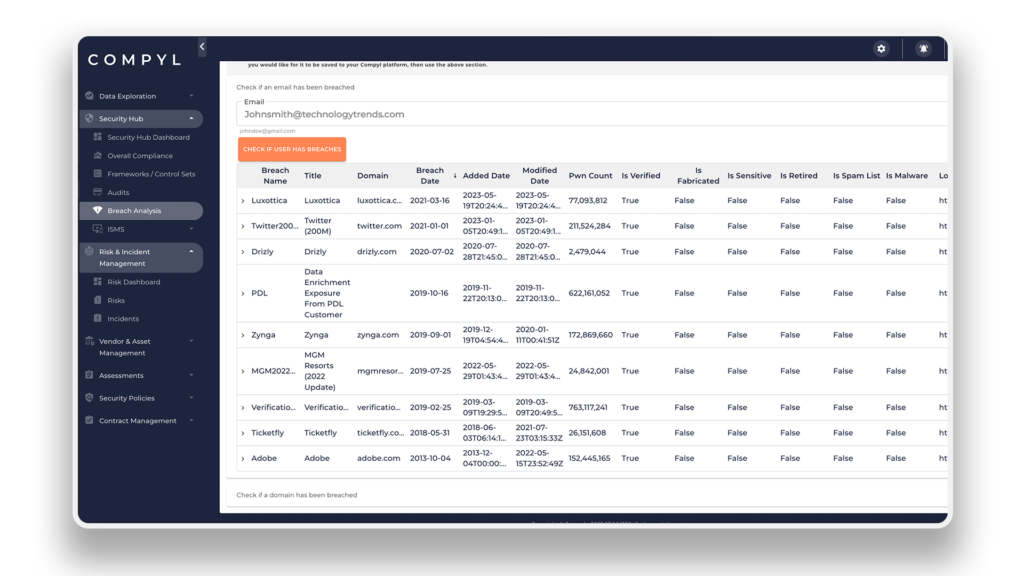
If you’re eager to gain insight into your organization’s exposure and ensure the safety of your users and domains, the Breach Analysis capability will be very handy for you. Introducing our brand-new Breach Analysis tool, powered by the “Have I Been Pwned” database. With this cutting-edge tool, you can quickly assess any potential breaches associated with your users and domains in real time.
At Compyl, we understand the criticality of staying informed about security breaches that may impact your organization. With the Breach Analysis tool, you can easily delve into aggregated data from various sources and breaches, then pull them into custom dashboards or reports to monitor and share with key stakeholders. This powerful integration allows you to perform on-the-fly assessments, ensuring that you stay ahead of potential threats and take proactive measures to protect your organization’s sensitive information.
Enhanced Contract Management
With our latest update, we have simplified the contract management process to a whole new level. If you’re already using Adobe Sign, you can now seamlessly link agreements directly into Compyl, streamlining the way your team handles contracts.
By linking agreements directly, you eliminate the need for tedious manual data entry and ensure data consistency between systems. Any updates or changes made in Adobe Sign automatically reflect in Compyl, keeping all stakeholders aligned and informed in real-time. This seamless synchronization minimizes errors, enhances efficiency, and reduces the risk of miscommunication.
The streamlined contract process enables your team to collaborate more effectively. With contracts easily accessible within Compyl, team members can view, review, and comment on agreements in a centralized environment. This collaboration fosters greater transparency, accelerates decision-making, and ensures that contracts progress smoothly through the approval and execution phases.

Dynamic Dashboards and Comprehensive Reporting
In today’s data-driven world, the ability to harness the power of information is key to success. At Compyl, we firmly believe that data is power, and we are excited to provide you with the tools to unlock its full potential. With our integrated Business Intelligence (BI) tools, you can leverage the data that Compyl has access to and create customized dashboards and reports, bringing clarity to your security posture like never before.
Imagine having a comprehensive view of your organization’s security landscape at your fingertips. Our BI tools empower you to transform raw data into meaningful insights, allowing you to make informed decisions and take proactive measures to protect your valuable assets. By tapping into the vast data resources within Compyl, you can build out customized dashboards tailored to your specific needs and priorities.
With our user-friendly interface and intuitive drag-and-drop features, designing interactive dashboards becomes a breeze. You can select the data points that matter most to you, whether it’s incident trends, risk assessment scores, compliance status, or any other relevant metrics. These visually appealing and dynamic dashboards provide real-time updates, giving you a holistic view of your security posture and enabling you to identify patterns, trends, and areas that require attention.
But the power of our BI tools extends beyond dashboards. You can also generate detailed reports that delve into specific aspects of your security program. Whether you need executive summaries, compliance reports, or incident analysis, our integrated BI tools empower you to generate professional-grade reports with ease. These reports provide actionable insights that support strategic decision-making, help you communicate your security program’s effectiveness to stakeholders, and ensure alignment with industry standards and regulatory requirements.

Revolutionize your security program with Compyl’s groundbreaking V5.0.0 update, featuring new capabilities and AI-driven functionality for unmatched efficiency and effectiveness. Learn if Compyl is the right solution for you by requesting to see a demo from one of our Information Security Experts.
We’re Here to Help You Get Started
Meet with a Compyl expert who will listen and learn about your business needs.




