The Vulnerability Management Lifecycle

Key Takeaways: Vulnerability Management Lifecycle If recent cyberattacks have revealed anything, it’s that organizations need … The Vulnerability Management Lifecycle

Key Takeaways: Vulnerability Management Lifecycle If recent cyberattacks have revealed anything, it’s that organizations need … The Vulnerability Management Lifecycle

A recent survey of 8,000 IT professionals and business leaders discovered that nearly 75% expected … 8 Ideas for Incident Response Tabletop Exercises

When it comes to business and finance, risk is unavoidable. It includes everything from cyber‑attacks … The Risk Management Lifecycle Explained
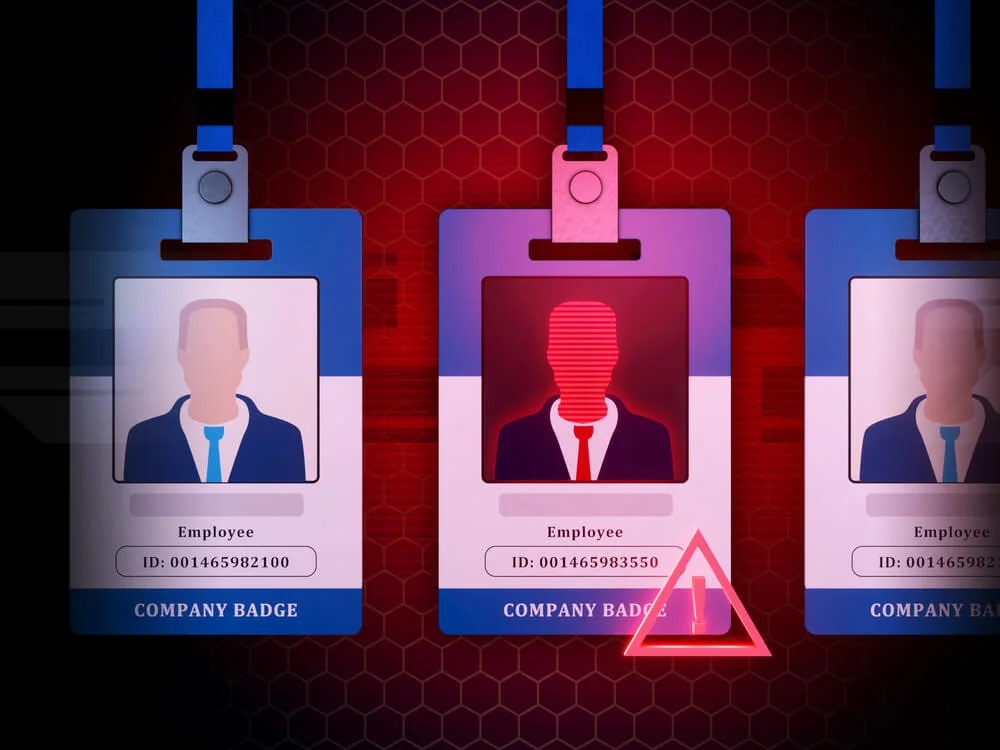
When you think of ransomware, data breaches, and other cyberattacks, what type of person comes … 10 Insider Threat Indicators To Be Aware Of

According to a recent report, over 80% of data breaches involve privilege misuse and infiltrations. … What Is Privilege Escalation?

In 2023, two of the largest casinos lost access to all system resources after a … 15 Vendor Risk Management Best Practices To Use

In today’s interconnected, digitally powered economy, minimizing and mitigating vendor risks is vital for financial … 11 Types of Vendor Risk

The number of risks that organizations must manage has grown significantly over the past decade. … A Helpful Guide To Risk Prioritization

Risks have never been more widespread, serious, and damaging to organizations than they are today. … What Is a Risk Management Committee?

Today’s enterprises view risks differently. Instead of reacting to adverse events after the fact, many … What Is Risk Tolerance?