Compyl 26.1 Is Live — See What’s New and How GRC Just Got Faster.
Conducting user access reviews in spreadsheets is tedious, time-consuming, and error prone. Automating the process frees-up valuable time, reduces risk, and strengthens your compliance posture
Use integrations to automatically pull user access data from all your systems
Schedule ad hoc or recurring review tasks based on requirements or preference
Assign review tasks to managers to assess whether the user's access is appropriate
Review access, add comments and tag colleagues to review and answer questions
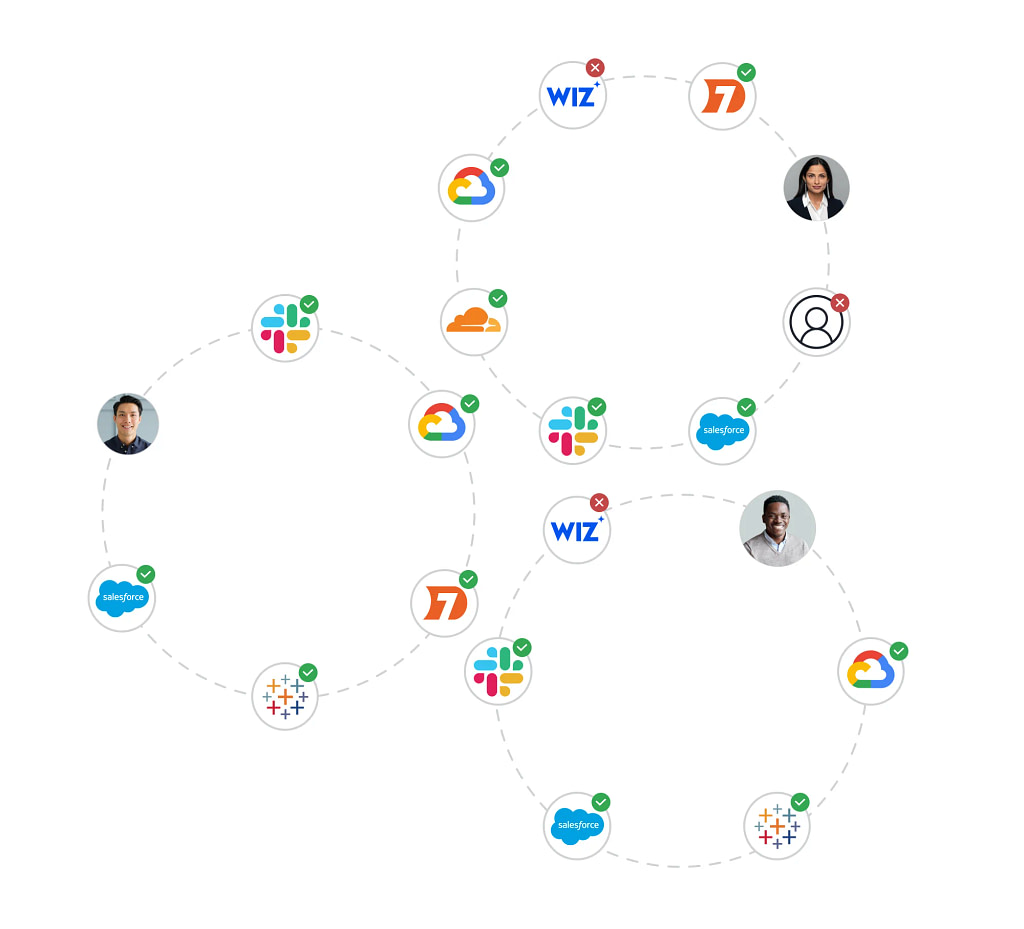
Take action on inappropriate access by creating an instant task to resolve it
Map access reviews to controls to ensure that compliance and security requirements are met
Eliminate blind spots by centralizing disparate system access data, enabling faster, more accurate reviews and reducing the risk of overlooked security issues.
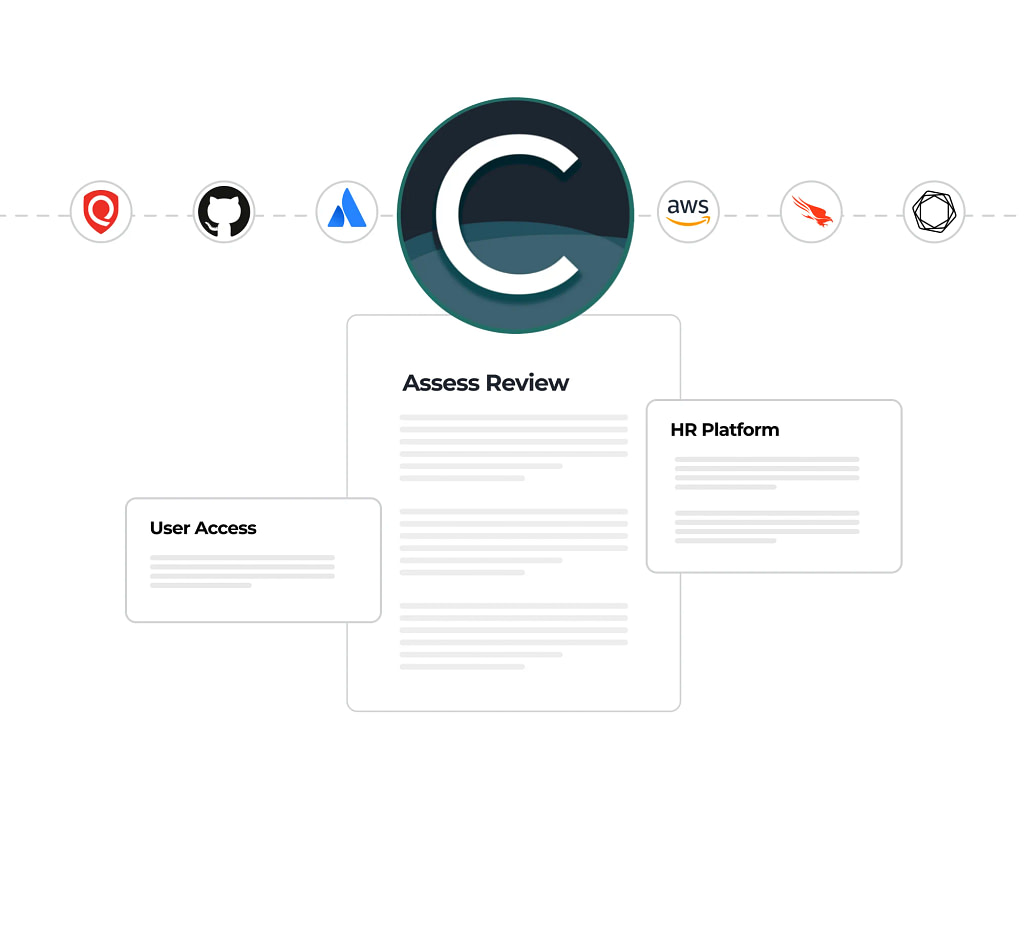
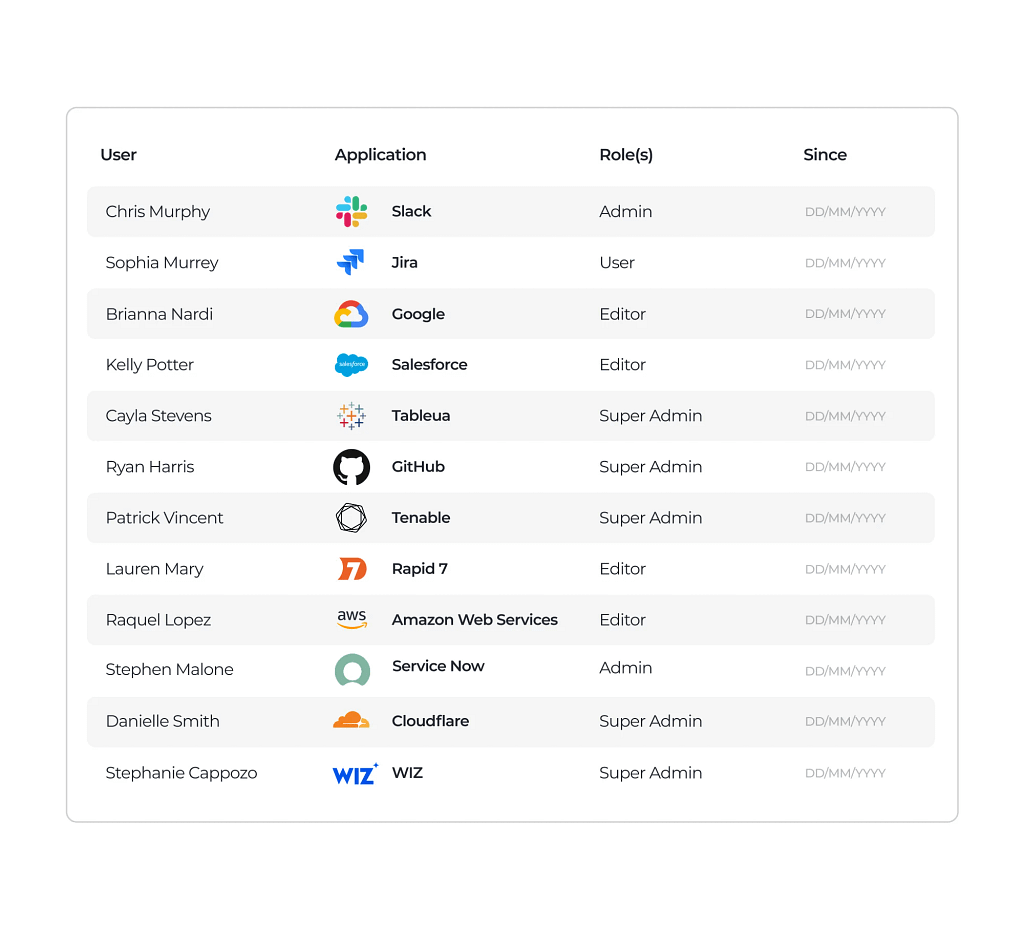
Replace tedious, error-prone spreadsheet reviews with automated access reviews that improve accuracy, ensure consistency, and free up your team for higher-impact work.
Catch and fix access issues due to overprovisioning, inappropriate or unused access sooner, by automating the review process to reduce the chances of overlooked permissions turning into security incidents.
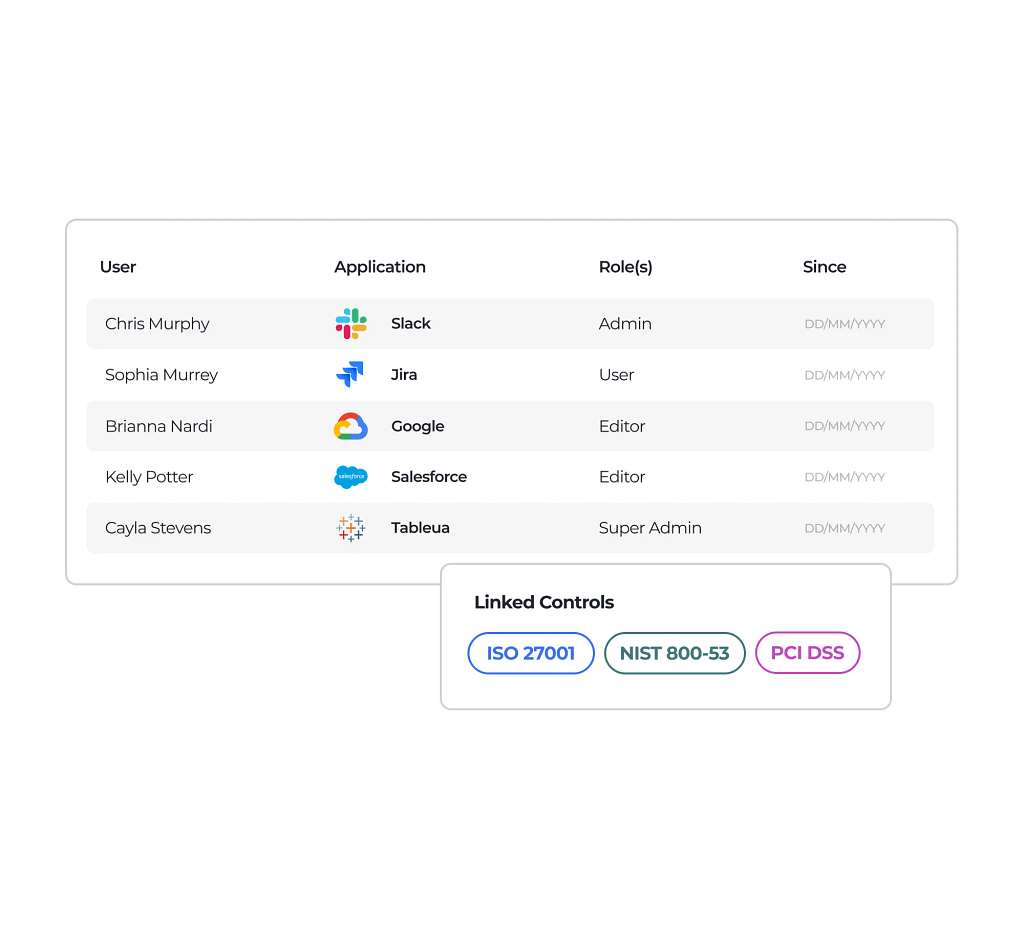
Stay compliant with standards like ISO 27001, PCI DSS 4.0, and NIST CSF by keeping access reviews on schedule and fully documented so when audit time comes, you can quickly show who had access, when it was reviewed, and what actions were taken.
Turn your data into deep GRC insights and AI-guided action with the flexibility you need to proactively manage risk, stay compliant and adapt to your needs—no heavy lift required.

Codes have been used for thousands of years to confirm someone’s identity, and modern passwords … Password Hygiene Best Practices
...
If your organization is like many companies, your employees use dozens of software-as-a-service applications on … 13 Common SaaS Security Risks
...
There were more than 2,800 data breaches in 2024, including nearly 750 attacks on the … What Is Credential Stuffing?
...